Oreilly - CISSP Certification Training: Domain 5
by David R. Miller | Publisher: Infinite Skills | Release Date: March 2016 | ISBN: 9781771376044
In this CISSP Certification Training: Domain 5 training course, expert author David R. Miller will teach you everything you need to know to prepare for and pass domain 5 of the Certified Information Systems Security Professional Certification covering identity and access management. This course is designed for anyone who is looking to prepare for the new CISSP certification exam.You will start by learning about identification and authentication, including password management, attacks on passwords, and biometrics. From there, David will teach you about single sign on and federated identity management. Finally, this video tutorial also covers authorization, including access control types, access control models, and controlling remote access.Once you have completed this computer based training course, you will have learned everything you need to know to successfully complete the Identity and Access Management domain of the CISSP certification exam.
- Identity And Access Management
- CISSP 2018 Domain 5 Update: Identity and Access Management (IAM) Part 1 00:12:42
- CISSP 2018 Domain 5 Update: Identity and Access Management (IAM) Part 2 00:13:12
- About The Instructor 00:03:34
- Introduction And Key Terms
- Key Terms - Part 1 00:07:12
- Key Terms - Part 2 00:07:01
- Identification And Authentication
- Provisioning - Part 1 00:08:13
- Provisioning - Part 2 00:07:02
- Provisioning - Part 3 00:09:39
- Identification And Authentication Mechanisms 00:09:43
- Something You Know - Part 1 00:07:45
- Something You Know - Part 2 00:08:16
- Something You Know - Part 3 00:08:04
- Password Management 00:08:27
- Attacks On Passwords - Part 1 00:10:02
- Attacks On Passwords - Part 2 00:08:05
- Authentication Protocols 00:07:49
- Something You Have 00:07:04
- Memory Card Smart Card 00:06:39
- Token Devices 00:06:55
- Challenge Response Token Devices 00:03:33
- X.509 Digital Certificates 00:05:50
- Something You Are 00:06:28
- Biometrics - Part 1 00:07:50
- Biometrics - Part 2 00:06:13
- Errors In Biometrics 00:06:11
- Multifactor And Mutual Authentication 00:06:21
- Single Sign-On And Federated Identity Management
- SSO And Federated Identity Management 00:08:00
- X.500 Directory Services - Part 1 00:06:42
- X.500 Directory Services - Part 2 00:07:41
- Kerberos - Part 1 00:08:11
- Kerberos - Part 2 00:09:42
- Kerberos - Part 3 00:06:31
- Sesame 00:06:23
- Federated Identity Management - X.500 00:09:09
- Federated Identity Management - SAML, OpenID, And IDaaS 00:09:18
- Authorization
- Authorization And Access Controls 00:10:59
- Access Control Types - Part 1 00:05:27
- Access Control Types - Part 2 00:10:29
- Access Control Types - Part 3 00:08:11
- Obscurity Layers Authorization Lifecycle 00:07:51
- Access Control Models - MAC - Part 1 00:09:33
- Access Control Models - MAC - Part 2 00:06:02
- Access Control Models - DAC - Part 1 00:08:31
- Access Control Models - DAC - Part 2 00:08:30
- Access Control Matrix 00:04:47
- Access Control Models - RBAC 00:07:37
- Access Control Models - Rule Based 00:06:53
- Centralized And Decentralized Access Control Models - Part 1 00:08:46
- Centralized And Decentralized Access Control Models - Part 2 00:02:34
- Distributed Hybrid Access Control Models 00:03:29
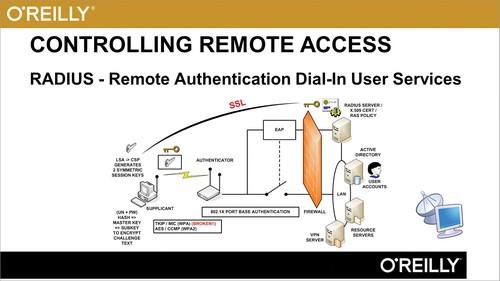
- Controlling Remote Access - Radius - Part 1 00:08:15
- Controlling Remote Access - Radius - Part 2 00:12:06
- Controlling Remote Access - TACACS Diameter 00:07:53
- Credential Management Content Context 00:08:34
- Additional Access Controls 00:08:57
- Attacks On Authorization 00:03:32
- Conclusion

TO MAC USERS: If RAR password doesn't work, use this archive program:
RAR Expander 0.8.5 Beta 4 and extract password protected files without error.
TO WIN USERS: If RAR password doesn't work, use this archive program:
Latest Winrar and extract password protected files without error.